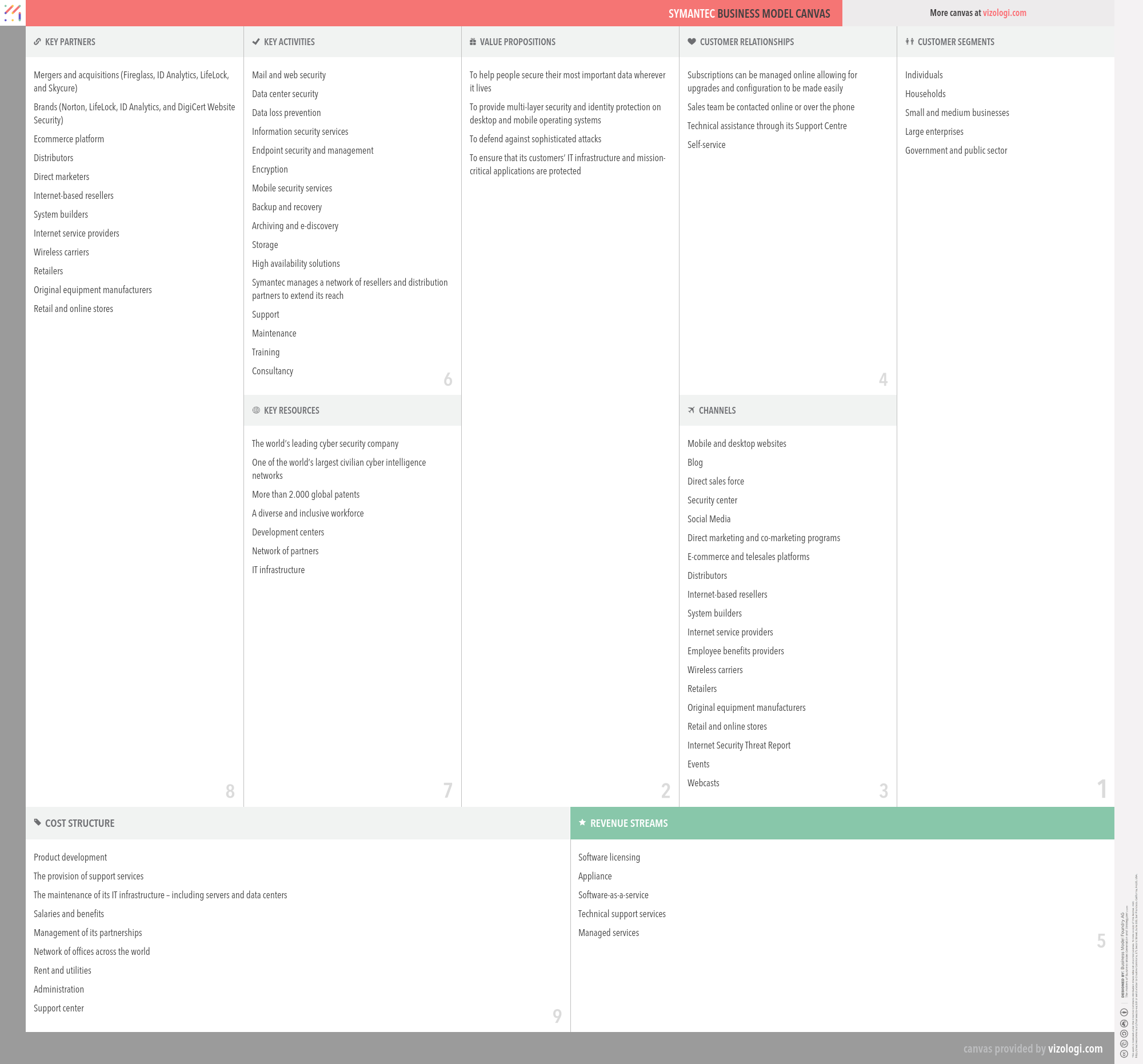
45 symantec antivirus best practices
LogicMonitor Security Best Practices | LogicMonitor Portal Security. The LogicMonitor platform includes many features that protect your data automatically. All information sent over the public internet is automatically encrypted in transit using TLS 1.3 encryption. Sensitive customer data—such as operating system versions, SNMP community strings, API passwords, device configuration files ... Symantec Antivirus configuration for vworkspace Profile Server Symantec Endpoint Protection (SEP) client should be installed on all computers on the network, including servers. On servers, SEP should be placed in appropriate client groups so that specific management policies and associated exceptions can be applied. Depending on the server's role, creating and applying the correct policies is critical for ...
Antivirus Best Practices For Complete Cybersecurity Below are antivirus best practices that can guarantee complete system protection, ensure normal day-to-day system functioning, detect and eliminate threats when followed to the letter. READ ALSO: Best Antivirus For 2022. Antivirus Best Practices Limit physical access to computers to few authorized users. Limiting access to computers can greatly ...
Symantec antivirus best practices
Recommended antivirus exclusions for Hyper-V hosts Configure the real-time scanning component within your antivirus software to exclude the following directories, files, and processes. Note If you are using Windows Defender as an anti-malware solution on your server, you may not need to configure additional exclusions. Symantec Endpoint Protection Best Practices for Planning and ... 3. Configure unmanaged clients to receive content from LiveUpdate Administrator. Best Practice for Endpoint Agents with Antivirus Protection Symantec OCR. With a typical antivirus program, excluding a folder prevents the AV program from monitoring data that are written to, or read from, the folder. Excluding a binary or executable file prevents the AV engine monitoring executable during read and write operations. It is recommended to whitelist all of the processes, files, and ...
Symantec antivirus best practices. Symantec Antivirus Corporate Best Practices - Experts Exchange If you do a search of these pages for "Symantec Antivirus Enterprise", you will find that a lot of folks around here have a lot of experience using the various forms of Symantec or Norton Enterprise. A very large number are strongly agains using it because of the difficulty in managing it and the level of resource intensity on the server and ... Best practices for Symantec Endpoint Protection Security best practices to stop malware and other threats Intrusion Prevention System best practices Security Threats 101 - Comprehensive resources to help you manage and resolve either detected or undetected security threats. Threat remediation Troubleshoot and respond to threats that may be on your endpoints. Symantec Antivirus best practice for vWorkspace components. Symantec Antivirus best practice for vWorkspace components. Hi Team , I am building infrastructure for Workspace Non-Persistence VDi. Infra build phase is almost complete and working fine which consist of connection Broker, Web access,File server,database server . now planning to deploy antivirus in each components. Broadcom Inc. (Customer) - Sign In - Support Portal Sign in with your Broadcom Inc. (Customer) account to access Support Portal ECX
Citrix Guidelines for Antivirus Software Configuration It should be noted that this configuration is typically regarded as a high security risk by most antivirus vendors. In high-security environments, organizations should consider scanning on both read and write events to protect against threats that target memory, such as Conficker variants. Scan local drives or disable network scanning. Technobezz - Tech Made Simple Technobezz is a global media platform, dedicated to technology. It’s the leading authority on price comparisons, informational guides, and independent reviews of the latest products and services. We make technology work for people; by connecting quality content and innovative ideas with the use of cutting-edge technology. Best Practices for Running Symantec Endpoint Protection 12.1 ... Best Practices for Running Symantec Endpoint Protection 12.1 on Point-of-Sale Devices Who should read this paper ... Antivirus, SONAR, Insight, and an Intrusion Prevention System (IPS). 2. The Application Control policy and System Lockdown to allow only approved applications. 3. The firewall policy to restrict access to specific applications. 10 Symantec Endpoint Protection Policy Best Practices - CLIMB In this article, we'll discuss 10 best practices for creating and maintaining a Symantec Endpoint Protection policy. 1. Use the default policies Symantec Endpoint Protection comes with a set of pre-configured policies that are designed to provide the best protection for your environment.
How to choose antivirus software to run on computers that are running ... When you configure your antivirus software settings, make sure that you exclude the following files or directories (as applicable) from virus scanning. This improves the performance of the files and helps make sure that the files are not locked when the SQL Server service must use them. Manage antivirus settings with endpoint security policies in Microsoft ... Antivirus Disk encryption Firewall Endpoint detection and response Attack surface reduction Account protection Microsoft Defender for Endpoint Firewall rule migration Tenant attach Encrypt disks Microsoft Tunnel Identity protection Conditional Access Endpoint protection Mobile Threat Defense partners Network access control Certificates Symantec Endpoint Protection - Best practices to ensure it provides ... The threat Landscape has changed and cybercrime is rampant. Companies cannot depend solely on desktop antivirus technology to protect themselves. Following the guidance provided here will improve the protection of desktops running Symantec Endpoint Protection and stop malware. Layer antivirus apps | App Layering - Citrix.com Symantec Help (SymHelp) diagnostic tool considerations. If you deploy Symantec Endpoint Protection in a layer, the Symantec Help (SymHelp) diagnostic tool requires that you place two files in Unified Endpoint Protection. Create a script with the following lines and place the path to it in a script path when you apply the Symantec layer.
Symantec antivirus Best practice for oracle database on windows server ... Symantec antivirus Best practice for oracle database on windows server 2003 — oracle-tech Oracle Communities Log In Register Home Categories Groups Events Resources Recognition Developer Center 3.9M Users 2.3M Discussions 7.9M Comments Home / Groundbreakers Developer Community / General Database Discussions / General Database Discussions
Best Antivirus Software for 2022 - CNET Dec 19, 2022 · In fact, it is one of the best antivirus software options. (Note: Microsoft changed the name of Windows Defender to Microsoft Defender and has expanded the service to other platforms.) This free ...
Antivirus Best Practices - social.msdn.microsoft.com Our office has recently deployed Symantec Endpoint antivirus to our desktops. We've noticed that the performance of Visual Studio has been hit pretty hard by this new antivirus package. I've been looking for some Best Practices or configuration docs/options to maximize the performance. But so far I've been unsuccessful and locating said resources.
Best Practices enabling Anti-virus Exclusions (4036144) Best Practices enabling Anti-virus Exclusions Description This article describes the exclusions that should be set when using Rapid Recovery with Anti Virus Software When using Anti Virus Software you should set certain exclusions on Real-time protection and Full System Scans (Scheduled or Ad-hoc).
Best practices for stopping malware and other threats Stopping malware and other threats. Symantec Endpoint Protection - Best Practices: The threat landscape has changed and cybercrime is rampant. The final defense against malware is a properly configured endpoint that deploys more than antivirus to provide layered protection and advanced policy configurations.
MDE Antivirus Configuration Common Mistakes and Best Practice Best Practices for AV Policy Settings: You may wonder what is the best Scan types for your daily scheduled scan on all systems, the Full Scan is for investigation of virus attack on the system, for the weekly or daily scheduled scan, it should be good and sufficient with quick scan.
CIS Controls v8 Released | SANS Institute Apr 21, 2021 · CIS Controls Cloud Companion Guide: CIS provides guidance on how to apply the security best practices found in CIS Controls v8 to any cloud environment from the consumer/customer perspective. CIS Provides Enterprises with Supporting Tools and Documents to Help with v8 Implementation: CIS Controls v8 provides backwards compatibility with ...
15 work-from-home security tips: Security best practices for ... - Norton Security software helps protect against other threats beyond computer viruses and malware. 4. Boost the security of your home router If you're working remotely even one or two days a week, you should strengthen the security of your home router and the Wi-Fi network it controls. This starts with creating a strong password for your Wi-Fi network.
Good cyber hygiene habits to help stay safe online | Norton Step 2: Use network firewalls Using a network firewall is another key habit for maintaining good cyber hygiene. Firewalls are a first line of defense in network security by preventing unauthorized users from accessing your websites, mail servers, and other sources of information that can be accessed from the web. Step 3: Update software regularly
Symantec Endpoint Protection Recommended Best Practices for Securing an ... It is best to provide the lowest level of privileges necessary to allow each user perform their normal tasks. Server IT-based Security Best Practice Configurations Limit end‐user write access to server volumes Many threats attempt to write themselves to file servers, thereby allowing quick spreading to other desktop systems that use these servers.
Tech Paper: Endpoint Security, Antivirus, and Antimalware Best Practices Tech Paper: Endpoint Security, Antivirus, and Antimalware Best Practices December 15, 2022 Author: Martin Zugec, Miguel Contreras Special thanks: Judong Liao, James Kindon, Dmytro Bozhko, Dai Li Overview This article provides guidelines for configuring antivirus software in Citrix DaaS and Citrix Virtual Apps and Desktops environments.
Broadcom Inc. | Connecting Everything Broadcom Inc, a Delaware corporation headquartered in San Jose, CA, is a global technology leader that designs, develops and supplies a broad range of semiconductor and infrastructure software solutions.
Symantec Antivirus Best Practice for Hyper-v 2012 R2 Cluster This can create an I/O storm on your hosts as well as saturate the CPUs as well. Look for products or settings that allow for randomization of full disk scans on the VMs or do not do full disk scans and only keep the real time scanners active on the VMs for incoming writes. 2. Watch for Antivirus products that update all the VMs at the same time.
Ransomware mitigation and protection with Symantec Endpoint Protection Most of the features to protect against ransomware in Symantec Endpoint Protection, are enabled by default. For more information on which features protect your environment, see: ... to minimize the amount of spam that reaches end-user inboxes and ensure you are following best practices for your email system, including the use of SPF and other ...
Symantec Security Center - Broadcom Inc. Symantec security research centers around the world provide unparalleled analysis of and protection from IT security threats that include malware, security risks, vulnerabilities, and spam.
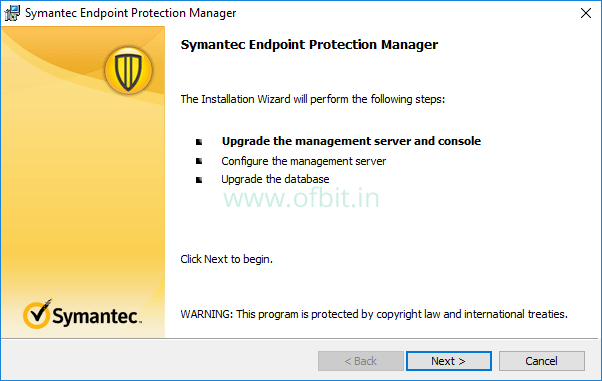
Best practices for upgrading or migrating to Symantec Endpoint ... Recommendations are to install all the SEP features on client operating systems like Windows XP, Windows 7 and Vista etc & At Server operating system can install only Antivirus & Spyware Protection. Best Practices for Installing Symantec Endpoint Protection (SEP) on Windows Servers 6.
Antivirus, VPN, Identity & Privacy Protection | McAfee The amount you are charged upon purchase is the price of the first term of your subscription. The length of your first term depends on your purchase selection. 30 days before your first term is expired, your subscription will be automatically renewed on an annual basis and you will be charged the renewal subscription price in effect at the time of your renewal, until you cancel (Vermont ...
Provisioning Services Antivirus Best Practices - Citrix.com Servers and targets may experience one or more of the following symptoms if antivirus software is not properly tuned for your Provisioning Services (PVS) environment: Target Device or Server appears sluggish or generally slower than normal. Prolonged, excessive CPU or memory utilization. Significant change in the Write Cache Disk I/O Performance.
Best Practice for Endpoint Agents with Antivirus Protection Symantec OCR. With a typical antivirus program, excluding a folder prevents the AV program from monitoring data that are written to, or read from, the folder. Excluding a binary or executable file prevents the AV engine monitoring executable during read and write operations. It is recommended to whitelist all of the processes, files, and ...
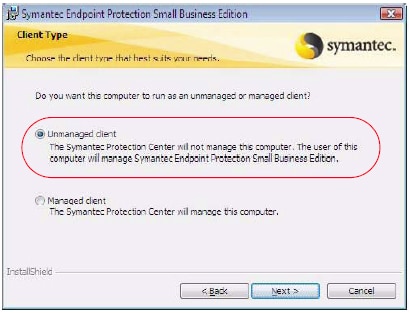
Symantec Endpoint Protection Best Practices for Planning and ... 3. Configure unmanaged clients to receive content from LiveUpdate Administrator.
Recommended antivirus exclusions for Hyper-V hosts Configure the real-time scanning component within your antivirus software to exclude the following directories, files, and processes. Note If you are using Windows Defender as an anti-malware solution on your server, you may not need to configure additional exclusions.














![Symantec: Endpoint Protection [product overview] | Infosec ...](https://resources.infosecinstitute.com/wp-content/uploads/2020/10/Symantec.jpg)















0 Response to "45 symantec antivirus best practices"
Post a Comment